
While Editor & Publisher was speaking to news publishers about their cybersecurity concerns in preparation for this feature, several significant events unfolded. Russia went on the offensive against Ukraine, invading the country and launching a war of choice.
At deadline, Russia’s war crime-mounting offensive was beginning its fourth horrific week, threatening to further destabilize the European continent and draw in the rest of the world, especially allied NATO nations. The televised and tweeted war put on worldwide display the bravery of journalists and the vital nature of information, especially in dire situations. At press time, three journalists have been killed reporting on the war.
On March 14, 2022, international news outlets reported that Israel's government systems had been disrupted by a cyberattack — a “digital denial of service” or “DDoS” attack. These aren’t particularly sophisticated hacks; they occur when the volume of traffic overloads servers. The source of the attack, if known, wasn’t disclosed, but news agency Haaretz reported that Israel’s ministries of health, justice and welfare were impacted.
What it meant for the public: every government site with the gov.il extension was out of service for over an hour, The Times of Israel reported that same day.
The Federal Bureau of Investigations (FBI) categorizes a number of cybercrime threats, from business email hacks to identity theft, spoofing and phishing scams, and ransomware.
Cybercrime recently came to the digital doorsteps of news publishers worldwide when PressReader, the digital supplier of more than 7,000 international magazine and newspaper titles, was hobbled by a cyberattack.
In the days following the outage, the developer reported, “We can now confirm that the network issues we experienced were caused by a ransomware attack. Immediately upon detection, our team implemented a comprehensive response plan to assess the threat and respond accordingly. As a defensive measure, we disable certain administrative and public-facing systems, which included taking Branded Editions sites and apps, as well as PressReader, offline.” The company added that they had no evidence that any customer data was compromised or that partner systems were impacted.
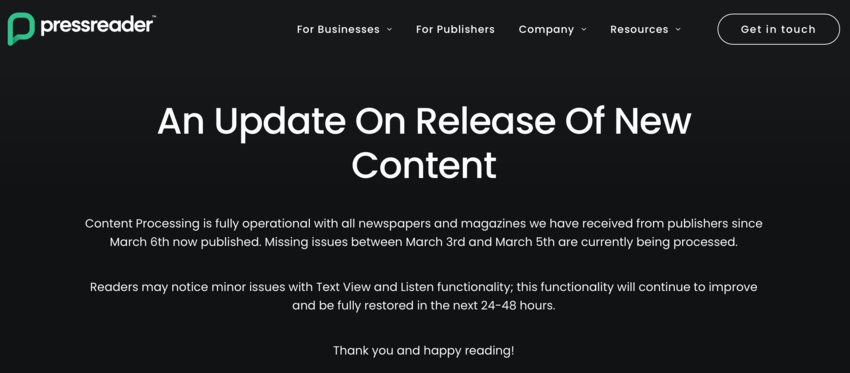
As our April issue was in production, “An Update On the Release of New Content” ran in stark white text across a black background on PressReader’s site. Thankfully, it reported that content processing was “fully operational, with all newspapers and magazines we have received from publishers since March 6 now published.” Still, they were in the process of restoring other issues and noted that readers may find the reading experience inconvenienced by “minor issues with Text View and Listen functionality.”
“We’re still working hard on getting operations up and running,” a company spokesperson told E&P.
The PressReader attack, the disruption in Israel, and the start of a war being waged by one of the world’s most notorious state-sanctioners of cyber warfare all came within just a month’s time. If you’re getting the feeling that cyberattacks are occurring more frequently and hitting closer to home, you're not wrong.

Daniel Tobok is the CEO of Cytelligence, one of the largest forensics and cyber-incident firms in North America. In 2020, the company was acquired by Aon. “We handle, on average, about 100 investigations per month, from ransomware to theft of intellectual property and extortion,” Tobok said.
Tobok also reported that attacks on media companies are escalating.
“Before the Ukraine-Russia conflict, they were about 5% of the crimes, but we’ve seen double-digit growth in [attacks on] news outlets and various media firms from what I call, ‘undetected sources,’” he explained.
It’s hard to pinpoint whether cybercriminals strategically target media companies or whether the criminal net is just so widespread that it ensnares news outlets almost incidentally. But news businesses around the world have found themselves on the receiving end of hacks, breaches and ransomware demands, perhaps the most insidious of them all.
In January 2022, Amedia, a Norwegian news company, disclosed it had suffered a cyberattack that shut down its subscription and advertising systems in late 2021. “On the night of Tuesday, December 28, several of Amedia’s central computer systems were shut down. The production of online newspapers is going as normal, but no paper newspapers will be published on Wednesday. This is because systems for publishing paper newspapers, advertisements and subscription management do not work as normal,” the company said in a statement.
In early February, News Corp reported that its email systems had been hacked, citing China as the culprit. Jim Waterson, media editor at The Guardian, reported, “The cyber-attack affected a limited number of individuals working for outlets including News UK — the publisher or the Times and the Sun — as well as the Wall Street Journal and the New York Post.”
Waterson had access to an internal News Corp email that described the attack as a “persistent nation-state attack,” he disclosed.
The year before, in June 2021, ABC-affiliated TV stations in Orlando, Florida; Charlotte, North Carolina; and Pittsburgh — owned by Cox Media Group — were knocked offline by a possible ransomware attack, though Cox Media didn't disclose the nature of the attack to the press.
Reporter Amiah Taylor explained ransomware — aptly named because it holds data hostage — in a February 17, 2022 article for Fortune.com. She cited research by SonicWall, an internet cybersecurity company, and its 2022 Cyber Threat Report, which offers some alarming statistics about ransomware attacks, in particular.
“Governments worldwide saw a 1,885% increase in ransomware attacks, and the health care industry faced a 755% increase in those attacks in 2021,” Taylor summarized the report.
“Ransomware also rose 104% in North America, just under the 105% increase worldwide,” the study indicated.
Naturally, news publishers — E&P's readers — are concerned about what it might mean for their organizations in the future and if they're well-guarded against cybercrimes.
Being proactive is a make-or-break measure.
“Ransomware has become the weapon of choice for various threat actors around the world,” Cytelligence’s Tobok told E&P.
Tobok said that two factions most often commit cybercrime. There are organized crime and then state-sponsored cybercrimes. The state-sponsored threats are primarily coming from Russia, Ukraine, China, North Korea, and lately, areas of the Baltics, he noted.
“It’s a fairly easy crime to commit,” he continued. “It’s low cost, and the profits are extremely high. To give you just a little bit of a fun fact, North Korea, in 2021, collected about $5.6 billion in proceeds from ransomware crime. When you think of a place like North Korea, which doesn't really have anything to export, yet they're able to generate $5.6 billion on this, you can understand why it’s attractive to criminals.”
Besides the financial motives, there are the strategic motivations that should concern news publishers, as well.
“What we’re seeing, especially when we get conflicts around the world and the geopolitical climate changing, they’re doing this in order to cause disruption,” he explained. Typically, the crooks are on the hunt for money, but some also steal data. Only a deep-diving forensic investigation can reveal whether data has been compromised, Tobok noted.
In the aftermath of an attack, victim companies will have two primary paths to take — “civil” versus “criminal,” Tobok calls them. On the civil side, the organization will need to investigate the breach, learn how hackers got in, make sure those doors are permanently closed and then endeavor to repair and restore systems.
As they go down the criminal path, the “three-letter agencies” get involved, and Cytelligence has relationships with all of them, Tobok said. A criminal investigation will be more concerned with saving "artifacts" that provide clues to the origin and scope of the crime.
“When we come across a client that has been hacked or breached, our first and foremost activity is preservation,” he said. “That takes a little bit of time. We preserve all the artifacts in a forensically sound manner and only then are we able to put the puzzle back together.
“But unlike the crime-scene investigations you see on TV — I have to warn you — we’re not as good-looking, and we don’t walk around in white coats and solve the crime in 28 minutes,” he quipped.
In other words, it can take a while.
“I chuckle sometimes when there is a national incident and some so-called cyber expert goes on TV and declares, six hours after the incident, that they know where the guys are from. It’s impossible,” he noted.
And Tobok noted that only about 25% of the time are the origins of the attack revealed, and that’s because cybercriminals have become adept at using spoofing and phantom servers.
Asked how news publishers might better protect themselves, Tobok offered some sage advice:
“When threat actors come across a server that’s encrypted, they will actually not touch it. It’s wasting their time, and for them, time is money,” he said.
“The doom and gloom is — it is happening, and it is real," Tobok stressed to E&P readers. “It’s not a question of if, but when. The good news is, by being proactive, you can minimize your chances of being breached, and that’s critical.”
Gretchen A. Peck is a contributing editor to Editor & Publisher. She's reported for E&P since 2010 and welcomes comments at gretchenapeck@gmail.com.
Comments
No comments on this item Please log in to comment by clicking here